Top Challenges in IoT Security: Insights from Forrester’s 2024 Report
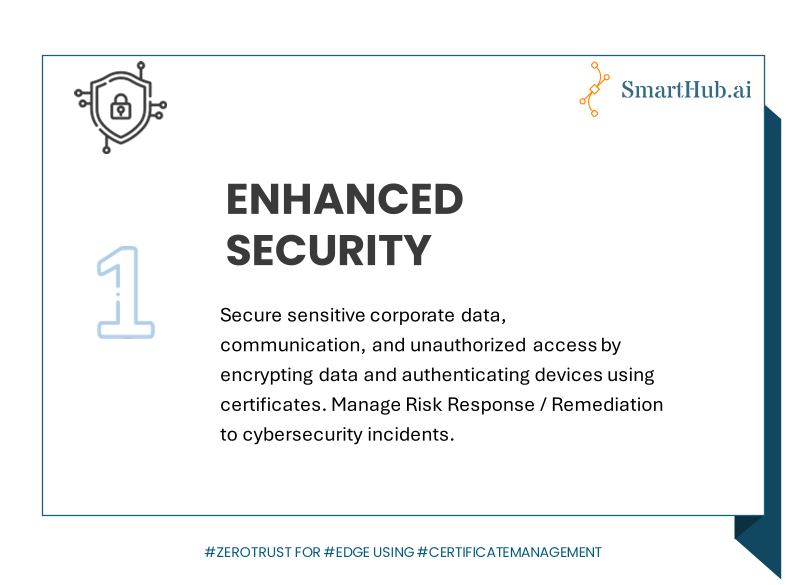
Article Solution Defend Solution Space Solution SpacesIn today’s hyper-connected world, where emerging threats lurk around every corner, securing Edge and IoT devices has never been more critical. Increase in global adoption of Edge / IoT devices is contributing to the rising cybercrime rates, as they become prime targets for cyberattacks. According to the recent Forrester report, the spotlight is on the […]
Top Challenges in IoT Security: Insights from Forrester’s 2024 Report Read More »