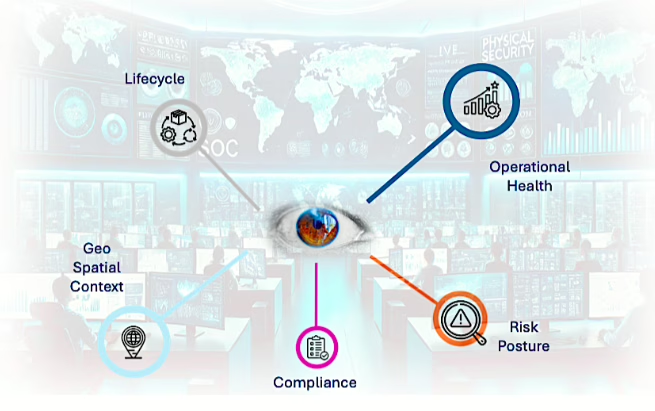
73% of CISOs Admit… Security incidents due to unknown or unmanaged assets is a huge headache
Article Blogs Smart Manufacturing Solution DefendOnce upon a time, the CISO was the firewall champion – emerging from deep within the IT trenches. Networking, servers, patching, endpoint security – these were their domains. And they’ve come a long way. From tech specialists to boardroom leaders, today’s CISOs speak the language of risk, regulation, and resilience. They sit at the intersection of […]