Next-Gen OT Security: Leveraging Agentic AI and AIoT for Resilience and ROI
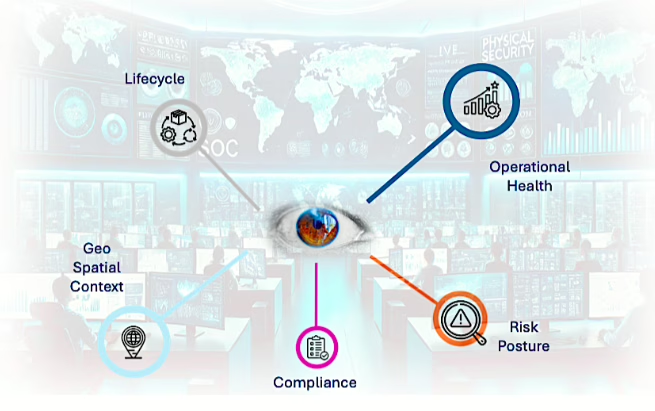
Article Blogs Smart Manufacturing Solution Defend UncategorizedOperational Technology (OT) is no longer operating in the shadows of IT—it’s now a mission-critical part of business continuity. Yet, as OT environments evolve to support always-on operations, real-time decision-making, and compliance mandates, they are also becoming increasingly fragmented, vulnerable, and complex to manage. OT infrastructures are often sprawling ecosystems of heterogeneous devices and sensors—from […]
Next-Gen OT Security: Leveraging Agentic AI and AIoT for Resilience and ROI Read More »