Author: Niranjan Maka
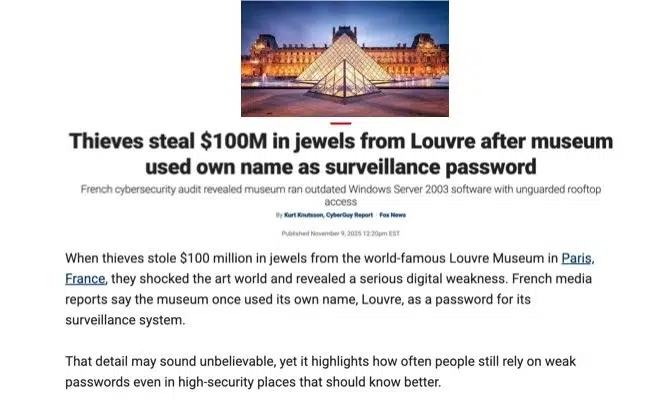
The Louvre Heist has been in the headlines. And CISO/CIO/CEOs don’t envy them.
𝑻𝒉𝒆 𝒍𝒂𝒕𝒆𝒔𝒕 𝒊𝒔 𝒕𝒉𝒆 𝒓𝒆𝒗𝒆𝒍𝒂𝒕𝒊𝒐𝒏 𝒕𝒉𝒂𝒕 “𝒔𝒕𝒂𝒏𝒅𝒂𝒓𝒅𝒊𝒔𝒆𝒅” 𝒄𝒓𝒆𝒅𝒆𝒏𝒕𝒊𝒂𝒍𝒔 𝒉𝒂𝒅 𝒃𝒆𝒆𝒏 𝒖𝒔𝒆𝒅 𝒂𝒕 𝒔𝒐𝒎𝒆 𝒑𝒐𝒊𝒏𝒕 𝒊𝒏 𝒎𝒂𝒏𝒂𝒈𝒊𝒏𝒈 𝒕𝒉𝒆𝒊𝒓 𝒔𝒆𝒄𝒖𝒓𝒊𝒕𝒚 𝒂𝒔𝒔𝒆𝒕𝒔
This is not surprising for many enterprise “operational” teams. They have seen it in their own environment and understand the huge challenges in trying to stay on top if this issue.
❗𝑪𝒉𝒂𝒍𝒍𝒆𝒏𝒈𝒆 #1: The teams are all different org units – like security/surveillance, factory floor team, facilities, AV/IT teams etc., They all have their own processes and, complying with InfoSec commandments is not the easiest as, they are responsible and measured for operational performance not just keeping their digital assets secure!
❗𝑪𝒉𝒂𝒍𝒍𝒆𝒏𝒈𝒆 #2: The sheer number / variety of vendors’ technologies is a huge challenge. Each Org Unit has it’s own sets of devices / models, management interface, patching schedules, maintenance requirements. Keeping track of just their own digital assets inventory and be on top of what needs to be done cutting across those vendor’ technologies is humanly impossible!
❗𝑪𝒉𝒂𝒍𝒍𝒆𝒏𝒈𝒆 #3: Translating CIO’s InfoSec guidelines and implementing them across their own digital assets defined by org boundaries, is no easy obstacle – what do those NIST controls mean, what does compliance guidelines translate to; or what is the mitigation or process to stay compliant? In the absence of enterprise level automation, the easy way out is to “standardise” on credentials, try to stay compliant with “one time, point in time audits”!
𝐴𝑛𝑑, 𝑖𝑓 𝑦𝑜𝑢 ℎ𝑎𝑣𝑒 𝑜𝑛𝑒 𝑑𝑖𝑠𝑔𝑟𝑢𝑛𝑡𝑙𝑒𝑑 𝑡𝑒𝑎𝑚 𝑚𝑒𝑚𝑏𝑒𝑟 𝑙𝑒𝑎𝑣𝑖𝑛𝑔 𝑦𝑜𝑢𝑟 𝑒𝑛𝑡𝑒𝑝𝑟𝑖𝑠𝑒 𝑎𝑛𝑑 𝑝𝑜𝑠𝑡 𝑎 “𝑠𝑡𝑎𝑛𝑑𝑎𝑟𝑑” 𝑐𝑟𝑒𝑑𝑒𝑛𝑡𝑖𝑎𝑙 𝑜𝑛 𝑡ℎ𝑒 𝑑𝑎𝑟𝑘 𝑤𝑒𝑏… 𝑦𝑜𝑢 𝑚𝑎𝑦 𝑏𝑒 𝑔𝑢𝑎𝑟𝑎𝑛𝑡𝑒𝑒𝑑 𝑡𝑜 ℎ𝑖𝑡 𝑡ℎ𝑒 ℎ𝑒𝑎𝑑𝑙𝑖𝑛𝑒𝑠!
There are ways to start sizing this problem, and put in place a process (based on tools that are available). If you need a quick half-hour chat on what are best practice checklists and where to start, message us.